Java is whole mess, always has been.
Further Java updates continue to break critical KVM over IP hardware and IPMI KVM with no respect or warnings to admins about how to ‘fix’ an stupid Java security problem during a real emergency. Sometimes you just need this hardware to work.
It is dangerous to disable all Java security, use your computer carefully. I’ve been doing this for decades without issue, don’t double click .CGI scripts you don’t recognize 🙂
To fix your KVM solution permanently, and completely DISABLE ALL JAVA SECURITY (until the next junky update where they break future functionality) just do this:
Step 1:
Find the java.security file, it’s here:
Windows: C:\Program Files (x86)\Java\jre1.8.0_321\lib\security
OSX: /Library/Internet Plug-Ins/JavaAppletPlugin.plugin/Contents/Home/lib/security
Linux: java.security -> /etc/java-8-openjdk/security/java.security or /lib/security
Step 2:
Completely remove everything you see in disabledAlgorithms:
DELETE:jdk.certpath.disabledAlgorithms=MD2, MD5, SHA1 jdkCA & usage TLSServer, \ RSA keySize < 1024, DSA keySize < 1024, EC keySize < 224, \ include jdk.disabled.namedCurves
DELETE THIS TOO:jdk.jar.disabledAlgorithms=MD2, MD5, RSA keySize < 1024, \ DSA keySize < 1024, include jdk.disabled.namedCurves
AND DELETE THIS:jdk.tls.disabledAlgorithms=SSLv3, TLSv1, TLSv1.1, RC4, DES, MD5withRSA, \ DH keySize < 1024, EC keySize < 224, 3DES_EDE_CBC, anon, NULL, \ include jdk.disabled.namedCurves
You may still need to edit your Java Configuration and add exceptions for your ‘http://’ URL’s
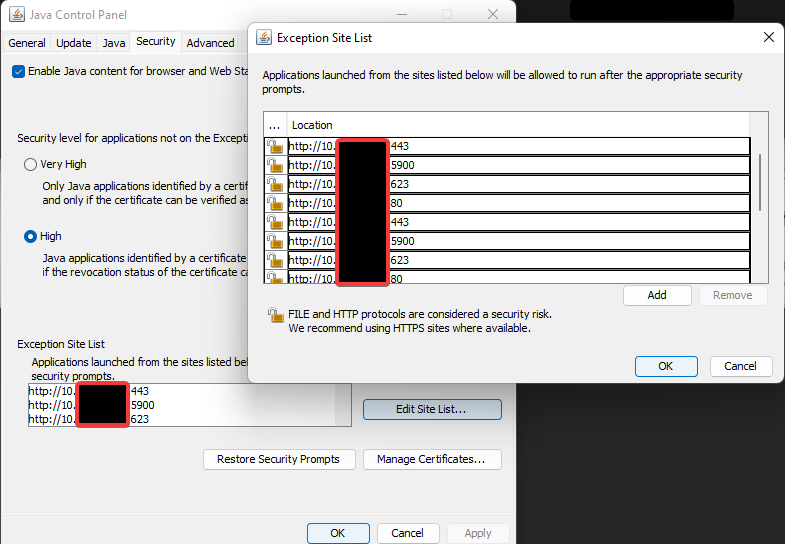
Word of warning:
This disables all the legacy checks, it’s a sledgehammer approach because I deal with a lot of different (aged) vendor hardware. Each of these aging devices is now on the ‘hazard list’ because of poor security/auth etc.
i.e. https://www.apc.com/au/en/faqs/FA333166/

Recent Comments